With the increasing adoption of Cloud environments and the rising tide of cybersecurity threats to digital data, establishing secure networks in the Cloud becomes imperative. Let’s explore how subnets ensure security in cloud networking.
A critical difference between a cloud network and an on-premises network
As anticipated, constructing a Cloud network closely resembles deploying a network in an on-premises data center. The primary distinction arises from the utilization of logical instances of networking elements in the Cloud, diverging from the reliance on physical devices. For instance, network interface controllers (NICs) transform into virtual NICs (vNICs) within cloud environments. Unlike traditional rack-mounted devices, Cloud networking delivers functions as services, showcasing a shift in the paradigm of networking infrastructure.
Subnets – Logically segmented cloud networks
When you start making a Cloud network, the first important thing is deciding how big it should be and what IP addresses it will use. This is like drawing the plan for your Cloud network and setting up its size and limits. These Cloud networks are then placed in different sections, like Virtual Private Cloud (VPC) or Private Cloud, which can be broken down into smaller parts called subnets. Imagine these subnets as organized sections in the big Cloud area. They are like building blocks, helping to structure and organize the Cloud environment smartly.

In simple terms, dividing the cloud into logical parts brings a big change. It gives users their private areas in the huge cloud space. This division is like how private clouds are secure, but it also lets things grow as they do in public clouds.
When we divide things this way, it’s important to carefully place important cloud things, like Virtual Machines (VMs), Virtual Server Instances (VSIs), storage, network connections, and load balancers. Using subnets cleverly helps users set up and run business applications in a way that feels like the usual setups we have in regular offices.
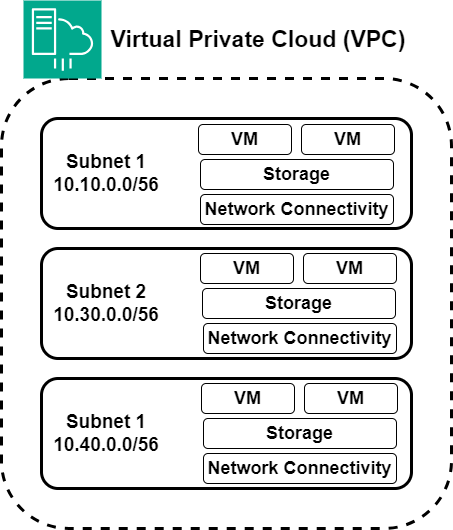
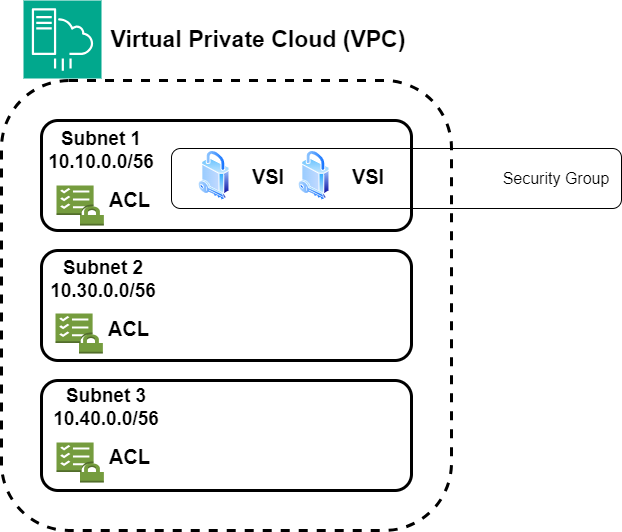
Very importantly, these subnets, aside from organizing things, are the main place where security happens in the cloud. Each subnet is like having its own security team. It’s made strong with access control lists (ACLs), which work like careful firewalls for the subnet. They pay close attention to how data comes in and goes out, making sure everything is controlled and safe.
In these subnets, the detailed design allows for making security groups that take care of security in a very detailed way. These security groups act like guardians of security for each specific instance. They’re like a customized defense system, especially protecting Virtual Server Instances (VSIs) and related things. After setting up the basic structure of a subnet, the next step is to add Virtual Server Instances (VSIs) and storage parts to it.
Accessing the Web from each subnet
Imagine you have an application with three parts: one for accessing the web, another for handling applications, and a third for managing the backend database. To keep things safe, we put the parts that deal with the web in one security group, the application parts in another security group, and the database parts in a third security group.
Now, since the parts dealing with the web need to connect to the Internet, we make sure they have access. We add public gateway instances to the network to let users reach the application on the Internet.
Even though these gateways are useful for Internet access, companies also want to connect their on-premises resources to the Cloud. They do this by setting up Virtual Private Networks, or VPNs, to link their office resources with the Cloud securely.
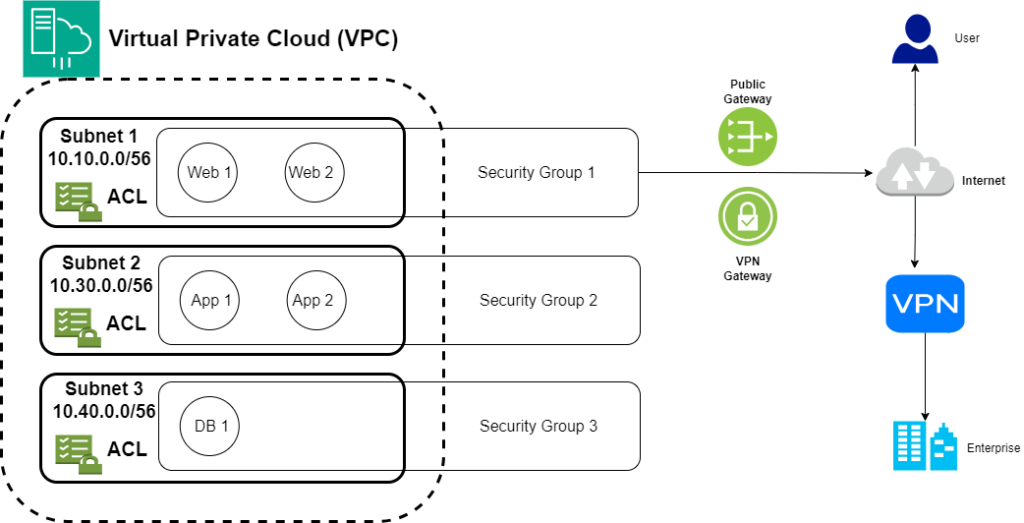
When creating lots of subnets and putting many tasks into action, it’s important to make sure that applications stay responsive. This is done using load balancers, which make sure there’s enough bandwidth available for the various applications.
Direct Link for hybrid cloud
Companies that use a mix of cloud and on-premises systems prefer secure and efficient dedicated high-speed connections between them rather than using public connectivity solutions. Some cloud providers, like IBM Cloud, offer this type of connectivity through solutions like Direct Link. It allows businesses to easily extend their on-premises resources to the cloud when necessary.
Conclusion
Constructing a Cloud Network involves establishing logical structures that provide networking capabilities similar to the familiar data center networks relied upon by IT professionals. These structures are vital for securing environments and ensuring optimal performance for essential business applications.
In the process of building a Cloud Network, IT professionals design these logical constructs to mimic the functionality of traditional data center networks. This ensures that the principles of security and high performance, crucial for safeguarding digital environments and supporting efficient business operations, are seamlessly integrated into the cloud infrastructure.


Leave a Reply